Hashicorp Vault is available as an option to provide credentials for Devo SOAR integrations and event types. The information required to obtain credentials from Hashicorp is stored in Devo SOAR secret engine records.
Devo SOAR currently supports KV secret engine.
To use Hashicorp for connections for integration and event types, follow this process in Devo SOAR, obtaining information as needed from Hashicorp:
Create a secret engine to store the information for your Hashicorp Vault account. Copy and paste the needed information from Hashicorp Vault.
Set up a connection for an integration or event type, selecting the appropriate Hashicorp Vault options. Verify that the connection is successful.
Open a playbook and add an integration or event type. As part of the configuration, select the connection you set in the previous step and specify a vault option for the Hashicorp credentials.
Add a Secret Engine
Navigate to Settings > Credentials Store.
Click New Secret Engine.
Enter a Name and ** Description**.
Copy the following information from Hashicorp Vault.
Approle ID Example: 7294b4d1-3f0a-4578-b68f-ba6d26a1c1b8
Approle Secret Example: e4396eda-569f-4297-8c90-5ea971568566
Approle path Example: https\://your-vault-address:8200/v1/auth/approle/login
Paste the values into the indicated fields on the New Secret Engine screen. For the Approle path, make sure to use an absolute path that starts with https\://
Devo SOAR supports Hashicorp KV secret engine v1 and v2. You can either create a new KV secret engine or use an existing one.
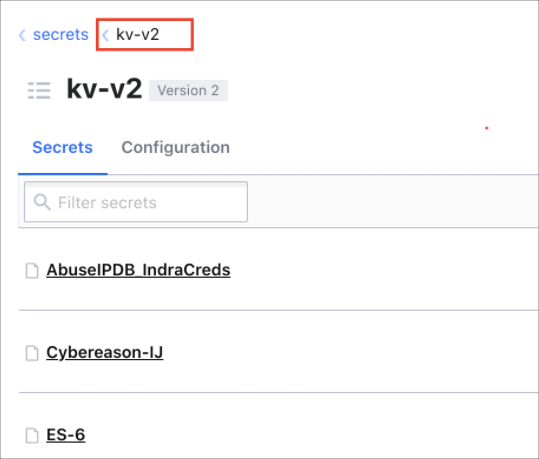
To configure to use a secret engine provide the relative path of that KV secret engine. Here in example, KV engine is created at path `secrets/kv-v2'
So you have to use kv-v2 in config
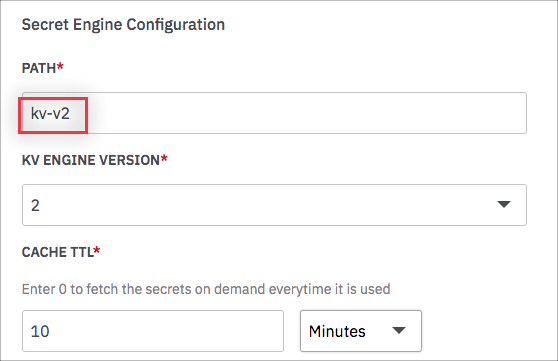
Scroll down in the Add Secret Engine screen to display the Secret Engine Configuration settings. Paste the relative path into the Path field.
Select the version of KV engine.
In the TTL field, enter the length of time you want to store the credentials in the Devo SOAR cache. If you enter 0, the credentials will be fetched from Hashicorp each time an authentication request is made.
Click Save.
Note: Check How to store credentials in KV secret engine at the section below to know how to store credentials in KV engine to be used by Devo SOAR.
The new credentials are saved, enabled, and listed on the Settings > Credentials Store page. You can now use credentials that are stored in your Hashicorp account for integrations and event types.
How to Store Credentials in KV Secret Engine
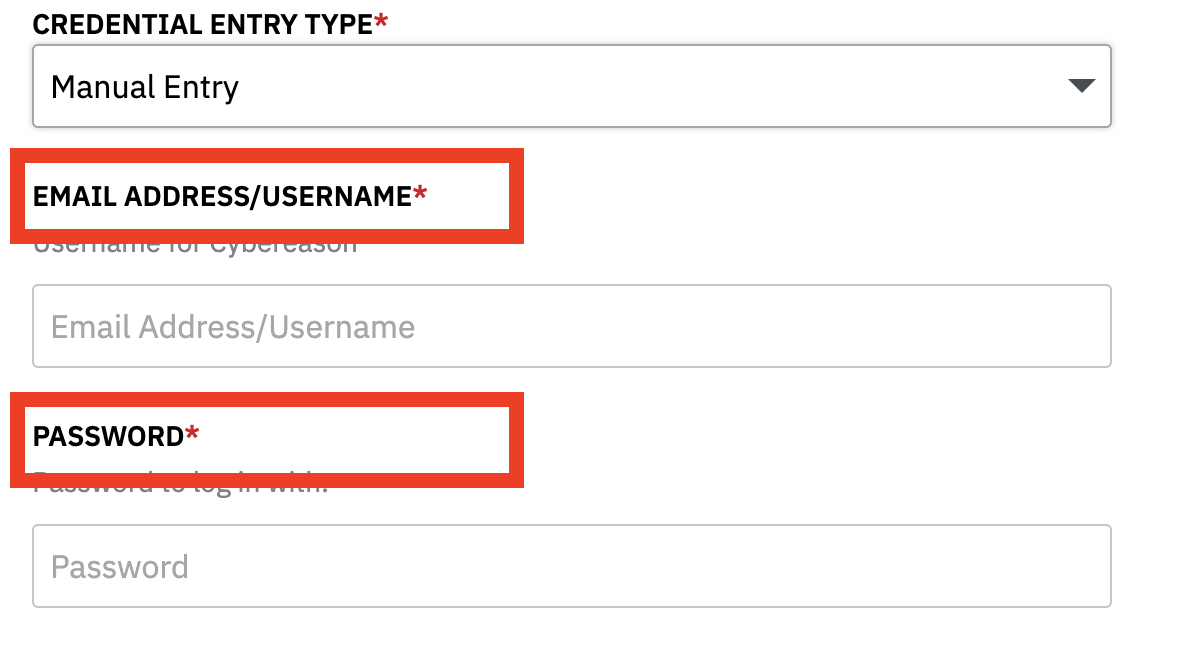
If you want to use credentials that you store in Hashicorp Vault, they should be stored in key-value pairs. The key should be the same as the labels of fields in the Devo SOAR UI. For example, Cyberreason uses username and password for credentials.
In Devo SOAR for Cyberreason Credential labels are as following:
Email Address/Username
Password
(* is symbol for mandatory fields )
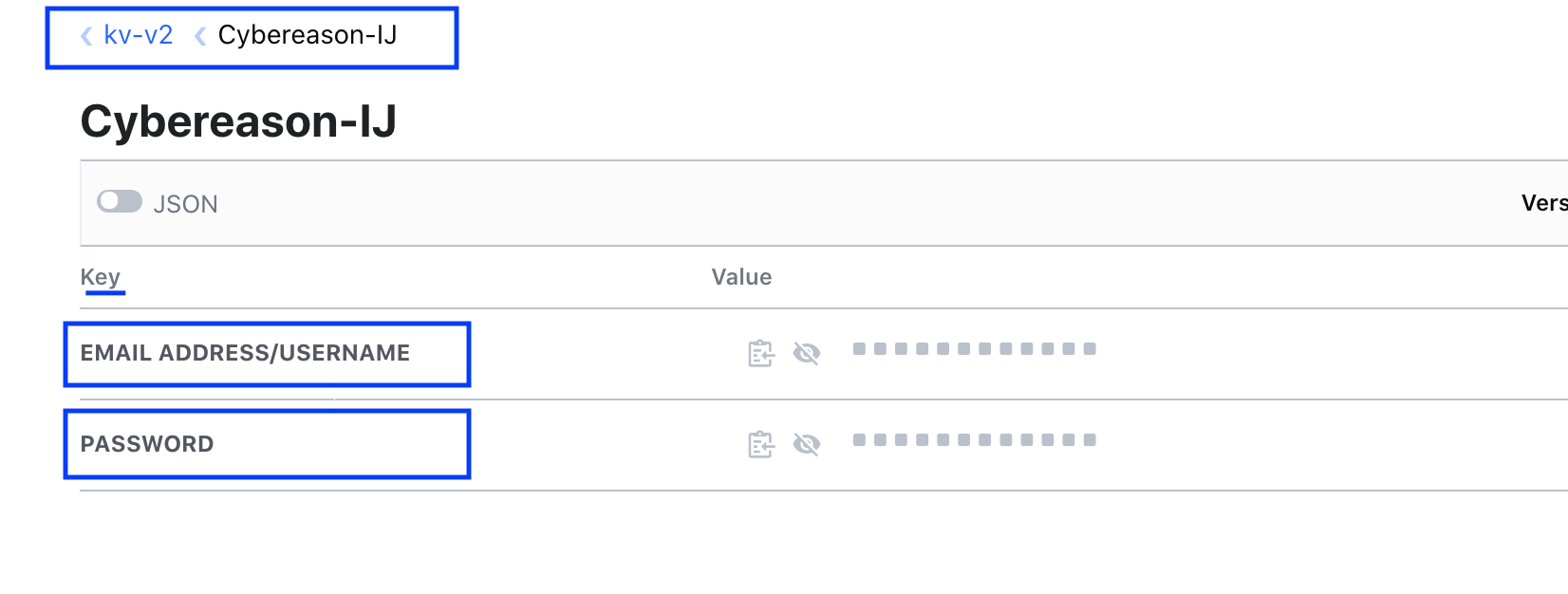
Correspondingly, in HashiCorp Vault, it should be stored as following (give any meaningful label for these, here it is Cyberreason-IJ in path "kv-v2")
key = Email Address/Username, Value =
key = Password, Value =
Set Up a Connection with Hashicorp Credentials
Access the connections setup in any of these ways:
On the Connections page, select New.
On the Automation > Integrations page, find the integration you’re looking for, click Details, and then click +.
From a playbook, add an integration, add a step and select the integration or event type you want to use. When prompted for a connection, select the option to create a new one.
For the connections setup, select one of these options:
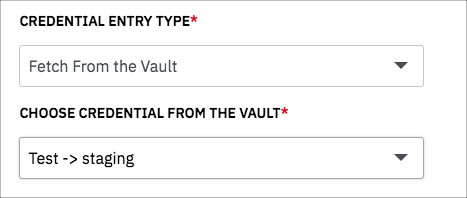
To obtain credentials from Hashicorp Vault, select Fetch from the Vault and then choose a credentials option from the dropdown list that appears.
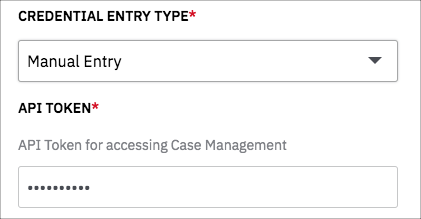
To use the credentials that are stored in Devo SOAR, select Manual Entry. When you select Manual Entry, the applicable parameters are displayed, as in the following example for which API Token is needed for authentication.
Note
If you want to use credentials that you store in Hashicorp Vault for manual entry, keep in mind that they are stored in key-value pairs. The key should be the same as the labels of fields in the Devo SOAR UI.
For example, case management uses API token. In HashiCorp Vault, it is stored as
key = API Token
Value =
To save the settings and connect, click Connect. When the connection is made, the integration or event type is available to be used in a playbook.
Example Use in Playbook
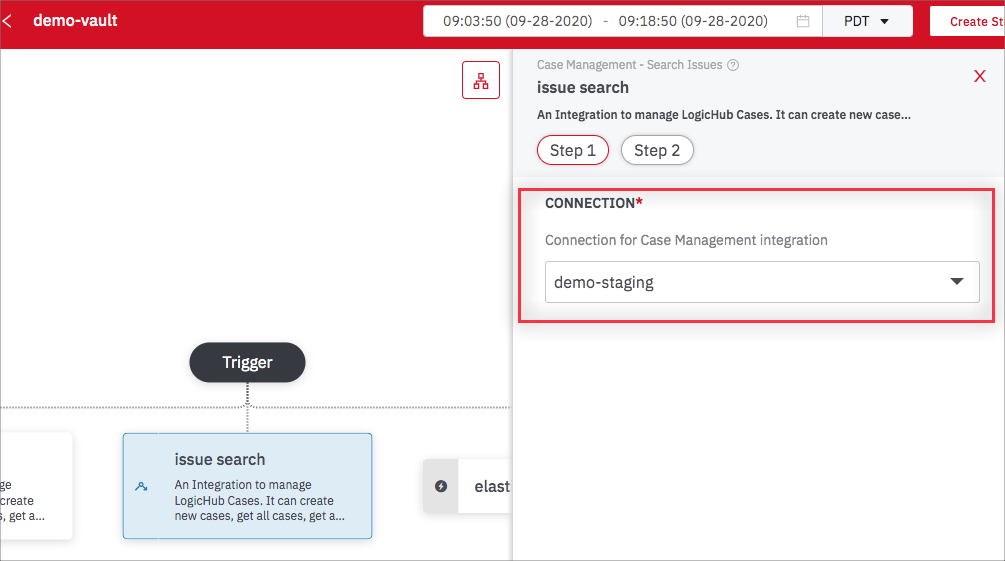
In the Easy Mode editor, search for the integration and select it. As part of the integration setup, select the connection that you set up. (If you haven’t yet created a new connection click Create a New Connection and follow the instructions in the previous section.)
Complete the setup and click Submit. If the connection is valid, the credentials are supplied automatically and the results of the integration are displayed in the results panel.
Manage Credentials
To manage your existing secret engines and create new ones, open the Settings > Credentials Store page.
Information about each is listed, including the secret keys that are used.
Perform any of the following actions from the More (...) menu.
Edit. Make changes to an existing secret engine.
Refresh. Update the credentials cache.
Disable. Disconnect the secret engine without removing the connection. If you edit a playbook that has a disabled engine, no new data is ingested. If you refresh the results table, an error message is displayed.
Enable. Restart an engine that was previously disabled.
Remove. Delete the secret engine from all of the connections that use it. The secret engine configuration is lost and cannot be recovered. All results that involve the engine will now fail.